Filter & Sort
-

-

Ants
-
Arms Race
-

Aspects of Cyber Conflict (pt. 1)
-

Aspects of Cyber Conflict (pt. 2)
-

Aspects of Cyber Conflict (pt. 3)
-
Aspects of Cyber Conflict (pt. 4)
-

Awareness is Key
-

Baking in Security
-
Brexit
-

Control Your Personal Data Stream
-
CreepingDataCritters
-

Cuckoo’s Nest
-

Cyber Specialists
-

Cybersexurity (pt. 2)
-
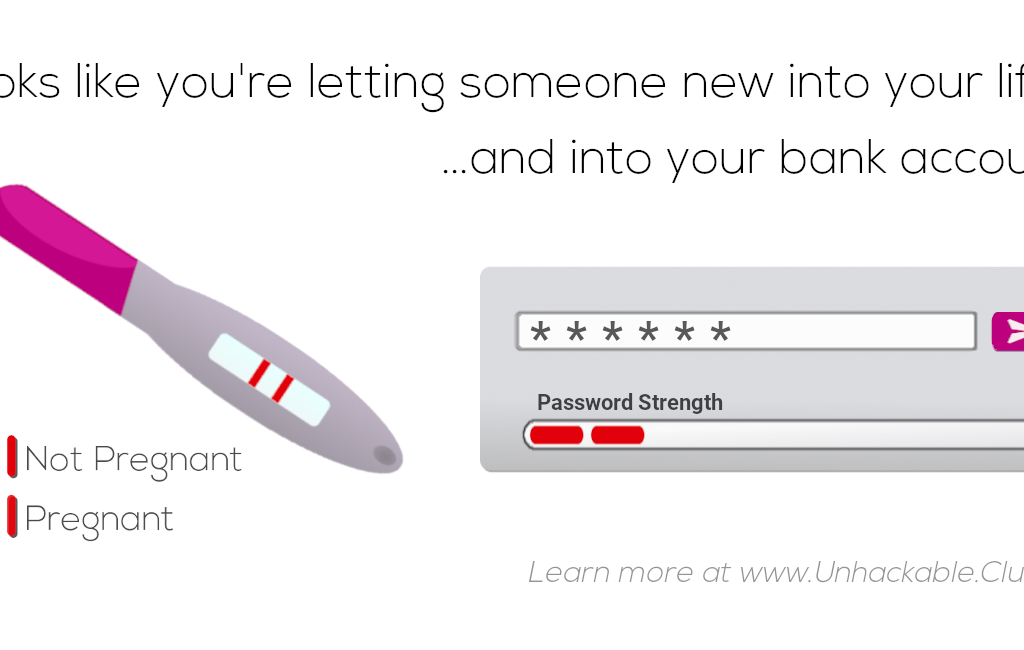
Cybersexurity (pt. 4)
-

Cybersexurity (pt.1)
-

Cybersexurity (pt.3)
-

D is for Dirk
-

Don’t Be an Easy Target
-

Free Smileys
-

Hackers
-
Hackers (pt. 1)
-

Hackers (pt. 2)
-
Hackers (pt. 3)
-

How Encryption Works
-
Internet of Things
-

Into the Rabbit Hole
-

Leaf
-

Lowest Hanging Fruit
-

M is for Marie
-
Malware
-
Mexico-USA
-
Modern Warrior
-

Moth (pt. 1)
-

Moth (pt. 2)
-

Mountain
-

My Other Computer (pt. 1)
-

My Other Computer (pt. 2)
-

My Other Computer (pt. 3)
-

My Other Computer (pt. 4)
-

My Other Computer (pt. 5)
-

My Other Computer (pt. 6)
-

My Other Computer (pt. 7)
-

My Other Computer (pt. 8)
-

My Other Computer (pt. 9)
-

Naked Without Encryption
-

Opt Out
-

P is for Piety
-

Personal Information
-

Phishing
-

Privacy
-

Secure Home (pt. 1)
-

Secure Home (pt. 2)
-

Security Measures
-

Smart Cities
-
Smoking Gun
-

So Long and Thanks for All the Phishing
-

Social Media Surveillance
-

The Era of Oversharing (pt. 2)
-

The Era of Oversharing (pt.1)
-

The Era of Oversharing (pt.3)
-

The Era of Oversharing (pt.4)
-

The Internet is not. Free (pt. 1)
-

The Internet is not. Free (pt. 2)
-

The Internet is not. Free (pt. 3)
-

The Internet is not. Free (pt. 4)
-
Tracking
-

Trust Your Instincts
-

VR Justice
-

Your Data is Safe

