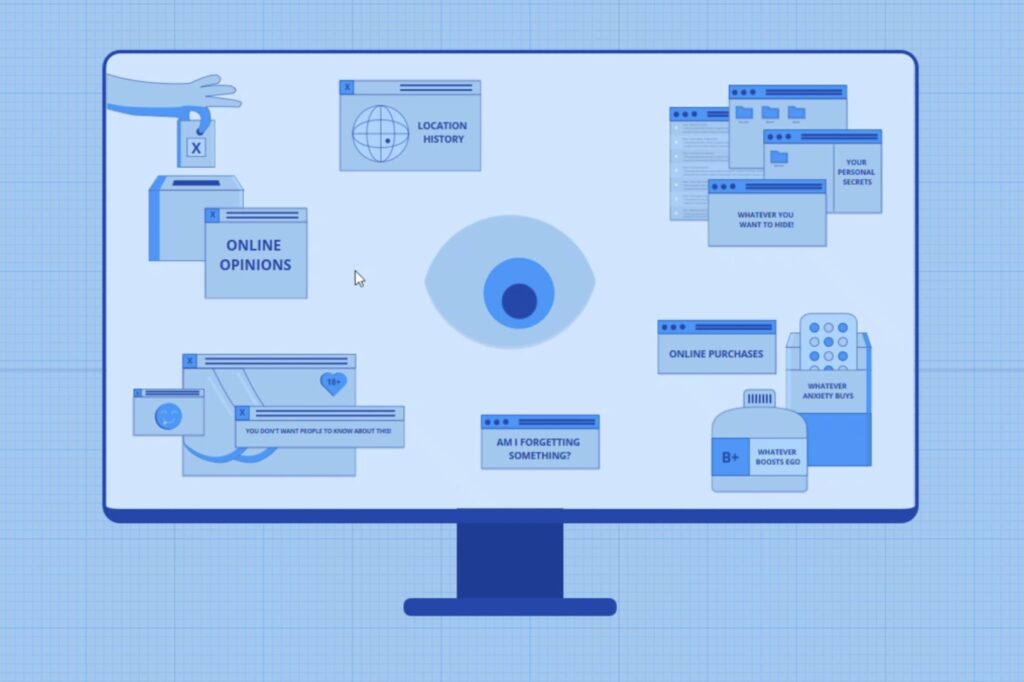
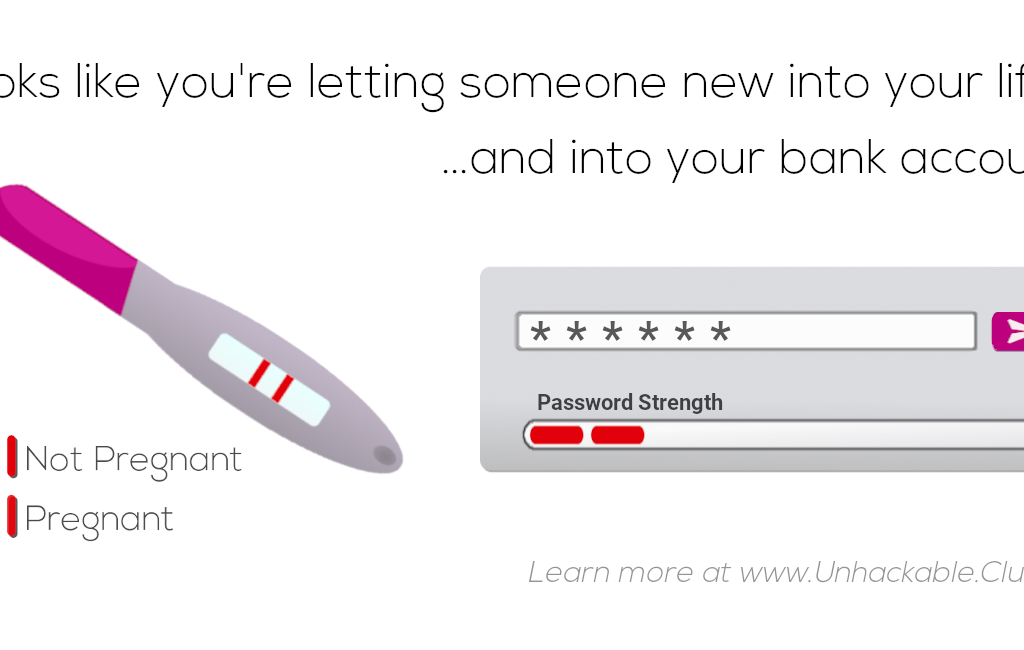
In the physical world, privacy is easy to recognize: a sealed envelope, a locked door, or a whispered conversation between two people. But in cyberspace, privacy is harder to see and often entails encryption—the process of encoding a message so that only authorized people can read its contents.