On Friday, February 26, the Center for Long-Term Cybersecurity participated in Mad Hacks: Fury Code Pitch Day, an event hosted and organized by the National Security Innovation Network (NSIN). The event was the culmination of a three week-long hackathon which challenged multidisciplinary teams to develop concepts, technologies, or systems to help human-controlled and autonomous vehicles operate through cyberattacks or other instances of electronic attack, and return to a known good state with or without human intervention.
The NSIN Hacks program offers students, academics, entrepreneurs and early-stage startups a rapid process to engage in collaborative problem-solving with U.S. Department of Defense (DoD) sponsors. NSIN holds hackathons around the country, each focused on a different challenge with applications to both Defense and private sector markets.
“Cybersecurity is a threat that connects all of the military’s priorities,” said NSIN Hacks Program Manager Kedar Pavgi. “We need a team versed in all angles of the challenge in order to shape the problem.” Participation in Mad Hacks: Fury Code spanned all 11 NSIN regions nationwide, with representation from over 50 universities.

CLTC Research Fellow and Daylight Security Research Lab Director Nick Merrill served as a mentor to four of the competing teams, answering questions and providing feedback to help each team further their idea along toward the pitch competition. Out of over 500 sign-ups and 70 hours spent working with mentors and partners, nine teams were selected as finalists to present their projects on Pitch Day. A panel of ten judges, including CLTC Executive Director Ann Cleaveland, from the military, academia, and private industry evaluated the finalists based on the viability of proposed solutions which were focused on at least one of three key areas: resilience, situational awareness/understanding, and sustainment and recovery.
Each team had a 5-minute pre-recorded pitch of their solution, followed by 5 minutes of live Q&A with the judges. The nine finalists included:
- Team RoadRunner
- PHC Defense
- Base8 – Secure Autonomous Network
- Team Distributed Spectrum
- SKY
- TM Pack
- SYN6 – Team Synergy
- Distributed Main Processor Design
- Feolayden Ventures
After all nine presentations, the judges deliberated on which four teams would win up to $25,000 in contracts to develop their solutions further and help the DoD end-users solve this mission-critical problem.

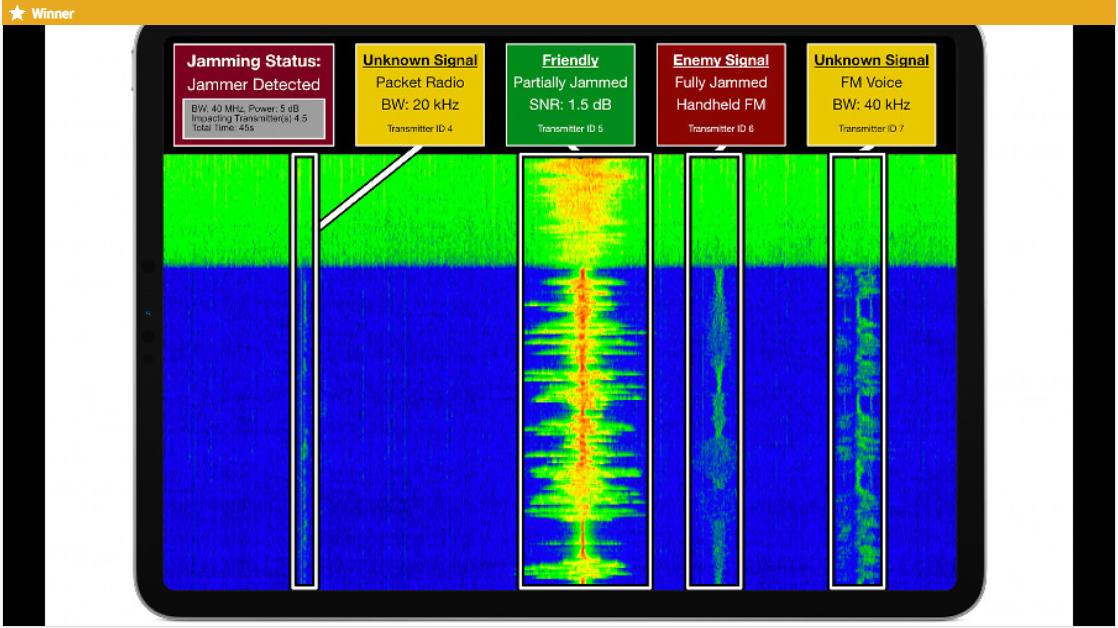
The Mad Hacks $25,000 grand prize winner was Team Distributed Spectrum and their RF Threat Detection System. This solution will detect cyber-attacks in the radio spectrum in real-time, as the RF Threat Detection system identifies enemy transmissions designed to disrupt vehicle operations and determine the threat they pose to the vehicle’s safety.
NSIN also awarded three other teams with awards of $15,000 each.
- Base8 – A team of students from San Diego State University and the University of Washington, Base8 provided a solution focusing on blockchain implementation to secure the network for an autonomous ground vehicle to ensure resilience, situational awareness, and recovery support.
- Team Koala-Proof – Team Koala-Proof includes six students, from five universities, in three time zones who collaborated for their PHC Defense solution is a collection of multiple solutions against cyber threats combined into a single system. This general solution allows flexibility in combating cybersecurity issues or a semi-autonomous or autonomous vehicle’s physical attack.
- Team Synergy – A collaborative effort, Team Synergy includes students and faculty from Cal State San Marcos, entrepreneurs, and retired military, pitched their Syn6 solution. Syn6 is an encrypted, compartmentalized, and intelligent three-tier cybersecurity architecture that maintains operational resilience for human-controlled and autonomous vehicles.